[vc_row][vc_column][vc_column_text]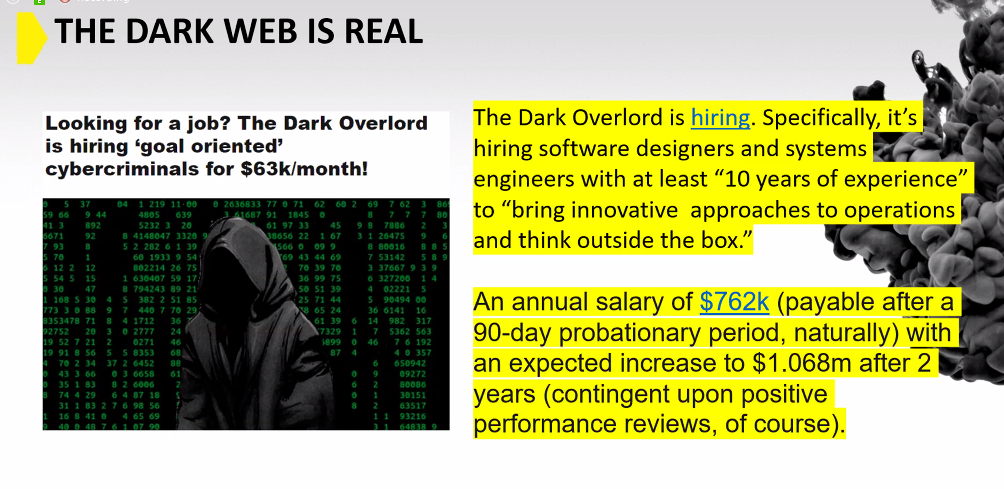
You may not realize it, but ransomware is a business. In fact it is a big business. Successful ransomware attacks can rake in millions of dollars. The groups behind ransomware operate with a corporate like structure, with their own newsletters, job boards, and even pay salaries.
A recent job ad found on the darkweb, was offering a six figure salary. These groups couldn’t afford to pay such large salaries if there wasn’t real money to be made.
These hacking collectives have many products available. Ransomware as a services, zombie computers, and of course your stolen data are all up for sale.
Your personal information is available as well. Yes, even items such as drivers license numbers, social security numbers and credit card numbers can be purchased. This information can be used to make purchases, open accounts in your name, or for other purposes.[/vc_column_text][/vc_column][/vc_row][vc_row][vc_column][vc_column_text]
What can you do?
No one would blame you for thinking that you should just give up and cancel all of your accounts. It would be easy to feel like there is nothing you can do to protect yourself. The truth is there are several things you can start to do, to not only fight back, but prevent your information from getting out there in the first place.
One.
Don’t use your actual credit card to make online purchases.
This may sound like an extreme step, but it is possible to not use your credit card to make purchases online. Privacy is a service you can sign up for, that will allow you to create virtual credit cards. You link our bank account to your privacy account and then you can make purchases.
You have control over your virtual credit cards. You can control the amount for each transaction, and can even create single use cards. You get the same fraud protection as using a real credit card.
Obviously you need to control access to your privacy account, but that isn’t difficult to do if you use the smart phone app. Most people don’t let their phone out of their sight, and the majority of phones are protected with a password, or face-id, or touch id.
Two
Do not reuse passwords.
Password reuse is a major problem. If you use one or two passwords, that are easy to remember and you use them often; you can expect them to be compromised. Once your email address is associated with a password, that account will be tested all over the internet.
Have a Netflix, or Hulu account? How about an Amazon or Spotify account? Your Apple or Google ID?
If you use the same email address and password for all of these accounts, you are setting yourself up for disaster. If a hacker can obtain your credentials for one site, they have access to all of your accounts.
This means not using your work email address and password either. Don’t mix the two ever.
Use a password manager and create unique, complex passwords for all of your accounts.
A password manager will allow you to copy and paste the password so you don’t need to be concerned with easy to remember passwords.
Most password managers also have a smart phone app, so whether you are mobile or in your home office, you have access to your passwords.
Three
Set up Two Factor Authentication
True. Two factor authentication can be a pain, but the extra step is worth it. I would rather deal with a few seconds of inconvenience, than spend hours or weeks trying to recovery from a compromised account.
There are two common types of two factor authentication. The first uses an application on your smart phone that generates a six or nine digit code that you enter after you put in your password. Enter the code correctly and you are permitted to access the site.
In lieu of using an application, you can receive a code via text message. The same process then applies, entering the code after you enter your user name and password allows you to log in.
If you fail to enter the secondary code, then you are denied access. If you have to many failed log in attempts then your account will be locked.
[/vc_column_text][/vc_column][/vc_row][vc_row][vc_column][vc_column_text]
More ways to stay protected.
We hope you find these three tips helpful in keeping your data out of the wrong hands. Don’t miss our recent post for 15 ways to Protect your Business from a cyber attack.[/vc_column_text][/vc_column][/vc_row]

